Equilibrium Infra Bulletin #32: Exploiting Sharded Blockchains, Privacy Infra Endgame, State of AA, and more...
Equilibrium Labs builds the state-of-the-art of decentralized infrastructure. We are a global team of ~30 people who tackle challenges around security, privacy, and scaling.
🔍 ShardDAG: Ordering and Exploitation in Sharded Blockchains
⚡️ Topic Summary
State sharding in blockchains amplifies existing problems around MEV exploitation and censorship as completing a transaction can involve block proposers in many distinct shards. This leads to more opportunities for exploitation. Punishing malicious behavior (exploitation or censorship) requires proving that 1) a specific shard had all the relevant data and 2) that it failed to process the data correctly.
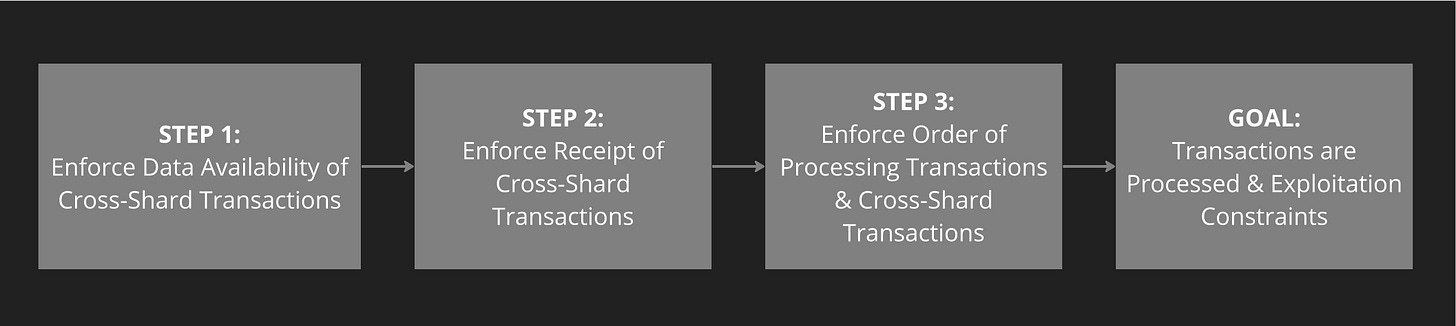
The steps to achieve verifiable cross-shard transaction data availability (source) To address this issue, Nil proposes ShardDAG; A DAG architecture that links shard blocks to each other and provides an enforceable order in which each shard must process cross-shard transactions (CSTs). This aims to constrain manipulation, exploitation, and censorship of transactions and CSTs.
The architecture relies on three main steps:
Ensuring cross-shard transaction data availability - All validators participate in a synchronization chain that aggregates and finalizes state updates from shards (each operated by distinct subsets of the total validator set).
Enforcing receipt of CSTs - The protocol specifies conditions on block validity and enforces receipt of CST via the synchronization chain.
Providing an enforceable partial order for transaction and CST processing - Validators should only sign a proposed block once they have verified that the block proposer has followed this protocol ordering.
🤔 Our Thoughts
While Ethereum has moved away from the state-sharding design, some L2 architectures, such as Nil’s zkSharding, leverage it to provide a unified protocol in which L2 dApps are composable yet scalable. Another example is L1 protocol Near, which has 6 shards on mainnet and recently transitioned to ZK sharding.
While ShardDAG can offer many benefits, it doesn’t come without tradeoffs. The two main ones are potential block size limitations (which can lead to delays in transaction processing) and additional complexity around block validity and transaction ordering.
More generally speaking, DAG-based architectures are becoming more popular again in blockchains. Implementations on the consensus level already include Sui (Mysticeti), Aptos (Shoal ++), and Aleo (Narwhal-Bullshark).
💡 Research, Articles & Other Things of Interest
📚 Do All Roads Lead To MPC? Exploring The End-Game For Privacy Infrastructure: Our latest research piece argues that if the desirable end-state is programmable privacy infrastructure that can handle shared private state without any single point of failure, then the trust assumptions of all approaches boil down to those of MPC.
📚 The State of Account Abstraction: Adoption of AA is increasing slowly, but surely.
📚 Espresso Open Sources HotShot Consensus Protocol: Aims to support thousands of nodes while retaining low latency, high throughput, and bribery resistance.

📚 Some Steps Toward Rollup Interoperability: An excellent overview of the current state of interoperability in the Ethereum ecosystem including issues, different solutions, their trust assumptions, and more.
📚 Near Chain Signatures Launch On Mainnet: Currently supports all blockchain protocols based on ECDSA elliptic curve (Bitcoin, Ethereum ecosystem, Near, etc) with EDDSA support coming later this year (Solana, Ton, etc.). The initial MPC network is comprised of eight validators, but Near aims to expand to 40+ over time.
🤌 Personal Recommendations From Our Team
📚 Reading: Technofeudalism - Yanis Varoufakis: Economist Yanis Varoufakis argues that capitalism is dead and a new economic era has begun: Technofeudalism. The twin pillars of capitalism - markets and profit - have been replaced with big tech's platforms and rents.
🎧 Listening: Crown - Elsa: Live performance at Dalston Lane Studios by the up-and-coming soul singer & songwriter from South London.
💡 Other: The Surveilled Society: Who is watching you and how: It’s interesting to see that surveillance is becoming an increasingly mainstream topic of discussion.






